What Exactly is SSH?
Let’s break it down. SSH, or Secure Shell, is a network protocol that acts as a digital fortress, safeguarding your ability to access other computers or devices over networks that might not be entirely secure. Think of SSH as your personal bodyguard in the digital world, ensuring that your sensitive data remains private and protected from prying eyes. Security is the name of the game, and SSH is the MVP when it comes to keeping your online interactions safe and secure.
SSH: The Ultimate Guardian in IoT Networks
When it comes to IoT networks, SSH is like the bouncer at an exclusive club, making sure only the right people get in. It’s the ultimate guardian, protecting your data from hackers and cybercriminals lurking in the digital shadows. With SSH, you can remotely configure and manage devices like Raspberry Pi, DragonBoard, or MinnowBoard running Windows 10 IoT Core without worrying about unauthorized access or data breaches.
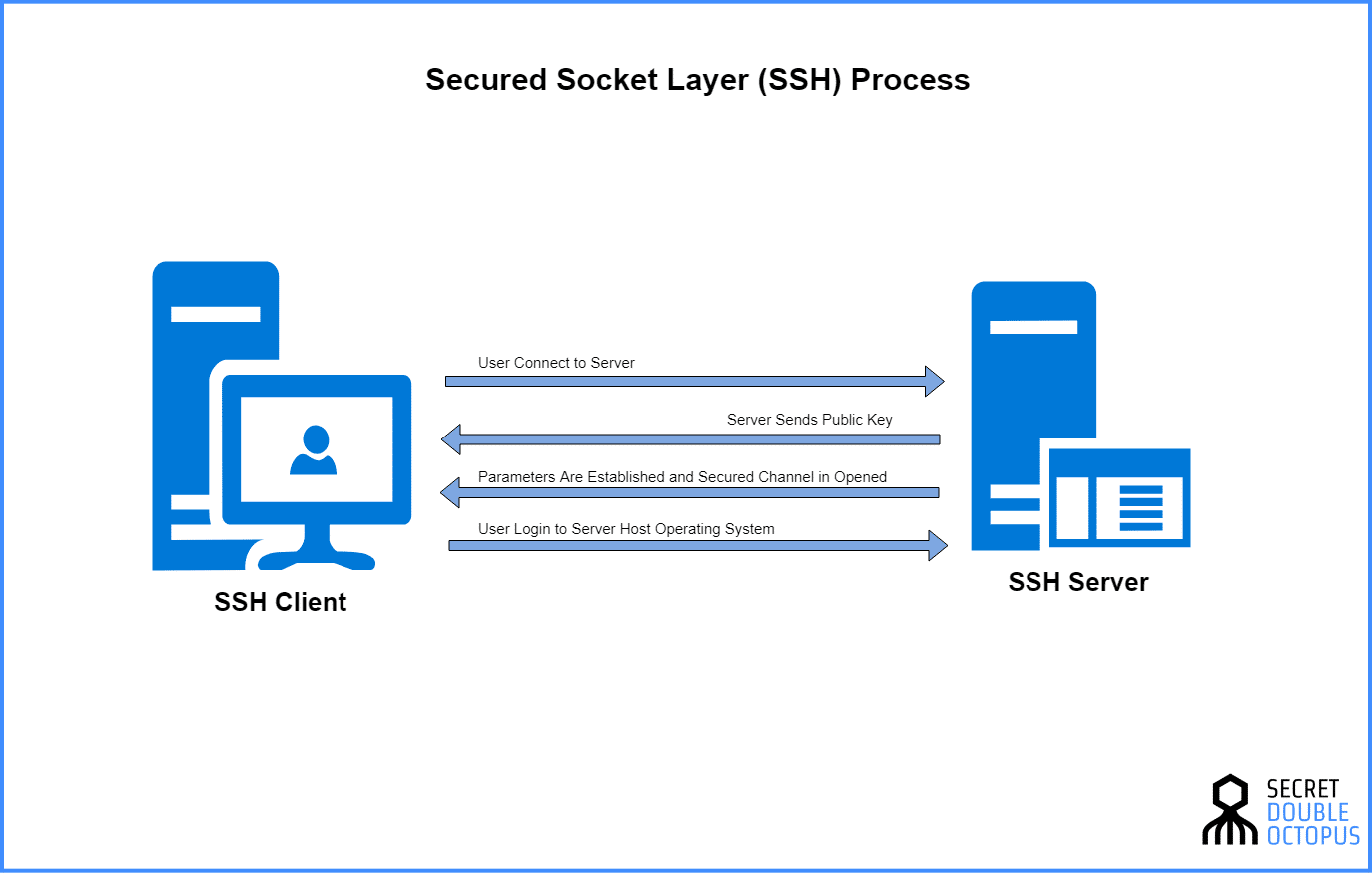
How Does SSH Work?
SSH operates by creating a secure channel between your device and the server you’re connecting to. It uses advanced encryption techniques to ensure that all data transferred between the two is protected. This means that even if someone tries to intercept your communication, they won’t be able to make sense of it. SSH also uses cryptography to authenticate connections, ensuring that you’re communicating with the right device or server.
Read also:Simon Cowell The Truth Behind The Rumors And His Legacy
Why Is SSH So Important?
In today’s interconnected world, where devices are constantly communicating with each other, secure communication is more important than ever. SSH plays a pivotal role in securing IoT networks by encrypting data and authenticating connections. Whether you’re managing servers, transferring files, or configuring devices remotely, SSH ensures that your actions are protected from potential threats.
Implementing SSH in IoT Networks: Challenges and Solutions
While SSH is an incredibly powerful tool, implementing it in IoT networks on Windows isn’t without its challenges. Setting it up correctly can be tricky, especially for those new to networking. For instance, ensuring that all devices are properly configured and that the network is secure can be a daunting task. However, with the right guidance and tools, these challenges can be overcome.
One common issue is ensuring that all devices in the network are compatible with SSH. Another challenge is managing keys and certificates to authenticate devices. But don’t worry—there are plenty of resources available to help you navigate these hurdles. From tutorials to forums, you can find all the support you need to successfully implement SSH in your IoT network.
SSH: A Cornerstone for Secure IoT Deployments
SSH is more than just a protocol; it’s a cornerstone for secure communication and management in the IoT landscape. Its ability to provide encryption, authentication, and secure remote access makes it an invaluable tool for securing IoT deployments. Whether you’re managing a small home network or a large enterprise system, SSH ensures that your data remains safe and secure.
SSH in Action: Remote Management Made Easy
With SSH, you can easily manage your IoT devices from anywhere in the world. All you need is an SSH client software, like PuTTY, on the system from which you want to connect. Once connected, you can configure settings, run commands, and even transfer files—all securely and efficiently. This level of control and flexibility is what makes SSH such a popular choice for IoT networks.
Why Choose SSH for Your IoT Network?
There are plenty of reasons why SSH is the go-to choice for securing IoT networks. For starters, it provides a secure channel over an unsecured network, encrypting all communication between your computer and the IoT device. This ensures that sensitive data, such as login credentials and commands, are protected from potential threats. Additionally, SSH allows for tunneling, or port forwarding, which enables data packets to cross networks that they wouldn’t otherwise be able to cross.
Read also:Exploring Leo Wus Love Life A Deep Dive Into His Relationships
Wrapping It Up
In conclusion, SSH is a powerful tool that plays a crucial role in securing IoT networks on Windows systems. It provides a secure way to access remote systems over unsecured networks, ensuring that your data remains protected from cyber threats. While implementing SSH might present some challenges, the benefits far outweigh the difficulties. So, whether you’re a seasoned IT professional or just starting out, SSH is an essential tool for securing your IoT deployments. Stay safe, stay secure, and let SSH be your digital guardian.