Hey there! Let’s dive into the world of AWS IoT and explore how you can take full control of your IoT devices from anywhere in the world. Whether you’re a seasoned IT professional or just getting your feet wet in IoT and cloud computing, this guide is designed to walk you through the process of setting up secure SSH access to your IoT devices. We’ll cover everything from creating tunnels to troubleshooting common issues, so buckle up and let’s get started!
Setting Up Secure IoT SSH Connections on AWS
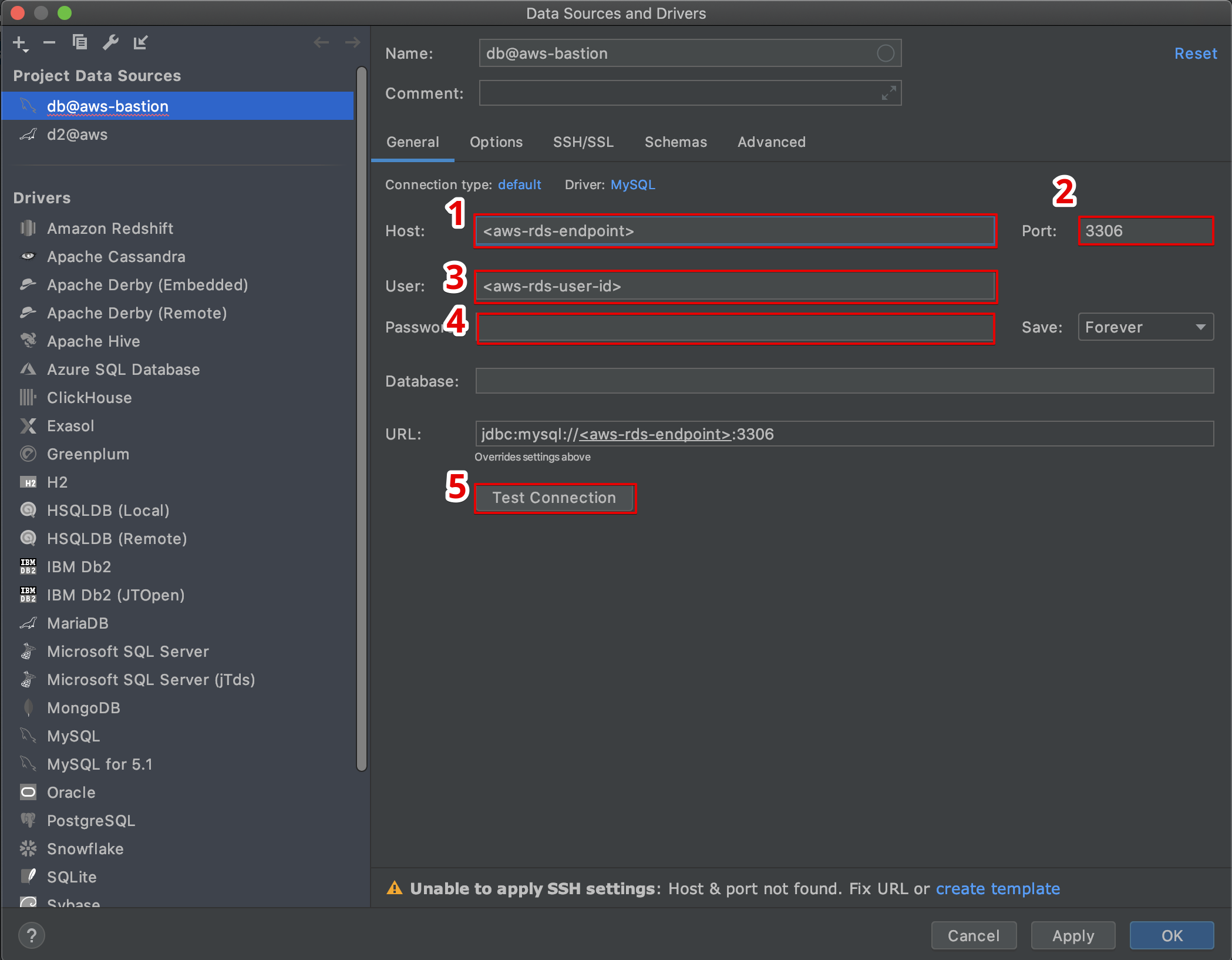
First things first, let’s talk about the quick setup method for rotating access tokens and SSHing into your remote devices directly from your browser. This method is not only convenient but also secure, ensuring that you have full control over your IoT infrastructure. To open a tunnel using this approach, you’ll need to create an IoT Thing in the AWS IoT Registry. For instance, you could name it something like "RemoteDeviceA." If you’re unsure about how to do this, don’t worry—there’s an example tutorial you can follow to open a tunnel and start an SSH session to your remote device.
Creating a Tunnel in the AWS IoT Console
When you create a tunnel from the Thing Details page in the AWS IoT Console, you’ll have the option to either create a new tunnel or open an existing one for that specific device. This flexibility ensures that you can manage multiple devices seamlessly. But before you dive in, make sure your devices are compatible with SSH and AWS IoT Core. You’ll also want to have a tool like PuTTY, OpenSSH, or any other SSH client of your choice ready to go. With these tools at your disposal, you’ll be well-equipped to take charge of your IoT devices from any corner of the globe.
Read also:Snowbird Brown The Heart Of Alaskan Bush People
Common Issues and How to Fix Them
Let’s face it—things don’t always go as planned. That’s why it’s important to be aware of common issues that might crop up when setting up IoT SSH connections on AWS. For example, you might encounter connectivity problems or authentication errors. Thankfully, AWS provides robust solutions to address these issues, ensuring that your setup remains secure and functional. We’ll go over some of these challenges and provide actionable tips to help you troubleshoot effectively.
Understanding IoT SSH Control on AWS
Now, let’s break down what IoT SSH control on AWS actually means. At its core, it’s about using the Secure Shell (SSH) protocol to manage and interact with IoT devices through Amazon Web Services. This method allows administrators to remotely access devices, execute commands, and monitor their performance—all while maintaining the highest level of security. By the end of this guide, you’ll have a solid understanding of how to set up IoT SSH control on AWS, complete with expert advice and practical examples to help you optimize your deployments.
Setting Up IoT Remote Access with SSH on AWS
Setting up IoT remote access with SSH on AWS involves several key steps. First, you’ll need to launch an EC2 instance and select an appropriate Amazon Machine Image (AMI). Next, you’ll configure security groups, set up IAM roles, and establish SSH connections. Each of these steps plays a crucial role in ensuring that your setup is both secure and functional. Let’s take a closer look at each step and why it matters:
- Launch an EC2 Instance: This serves as the foundation for your IoT setup, providing the necessary computing power.
- Configure Security Groups: These act as virtual firewalls, controlling access to your devices and ensuring that only authorized users can connect.
- Set Up IAM Roles: IAM roles define the permissions and access levels for your devices, helping you maintain control over your infrastructure.
- Establish SSH Connections: Finally, you’ll establish secure SSH connections to your devices, allowing you to manage them remotely.
Why IoT SSH Control on AWS Matters
IoT SSH control on AWS offers a robust solution for remote device management, ensuring secure access and control over your IoT infrastructure. Whether you’re a developer, IT professional, or simply curious about IoT security, this article has something for everyone. By mastering IoT SSH on AWS, you’ll be better equipped to streamline device management, automate processes, and ensure seamless connectivity between your IoT devices and the cloud.
Getting Started with AWS IoT Device Management
AWS IoT Device Management is a powerful tool that helps you register, organize, monitor, and remotely manage IoT devices at scale. By integrating with AWS IoT Core, you can easily connect and manage devices in the cloud. Additionally, AWS IoT Device Defender allows you to audit and monitor your fleet’s security posture, ensuring that your devices remain secure and compliant.
How Secure Tunneling Works
Secure tunneling is a critical component of AWS IoT Device Management. It allows you to establish secure connections between your devices and the cloud, ensuring that data remains protected during transmission. This method is particularly useful for updating firmware, performing remote diagnostics, and managing device configurations. By leveraging secure tunneling, you can keep your IoT infrastructure up-to-date and running smoothly.
Read also:Yumi Eto A Trailblazer In Art And Entertainment
Creating an IoT Thing in the AWS IoT Registry
To get started with AWS IoT, you’ll need to create an IoT Thing in the AWS IoT Registry. This Thing represents your remote device in the cloud and serves as the foundation for managing your IoT infrastructure. For example, you might name your Thing "RemoteDevice1." This Thing corresponds to the representation of your remote device in the cloud and provides a centralized location for managing its settings and configurations.
Best Practices for IoT SSH on AWS
Now that you have a solid understanding of how to set up IoT SSH connections on AWS, let’s talk about some best practices to keep in mind. First and foremost, always ensure that your devices are compatible with SSH and AWS IoT Core. Additionally, regularly update your access tokens and SSH keys to maintain the highest level of security. Finally, monitor your devices closely to detect and address any potential issues before they become major problems.
Conclusion
In conclusion, mastering IoT SSH on AWS is essential for successful IoT deployments. Whether you’re a system administrator, IoT developer, or technology enthusiast, understanding how to leverage AWS for IoT SSH control will empower you to take full control of your IoT infrastructure. So what are you waiting for? Dive in, explore the possibilities, and start building the IoT solutions of tomorrow—today!